Which Command Can Be Used to Determine a User's Most Recent Log in?
Linux is 1 of the most popular operating systems with an extensive user-base around the earth, most commonly programmers and developers. The open-source Unix-like operating organisation (OS) is rooted from the Linux kernel - an operating system developed by Linus Torvalds.
In uncomplicated words, Linux is a Unix clone, and its open-source feature allows anyone to change annihilation in Linux and redistribute it with your branding. These iterations of Linux are referred to as 'distros.'
Beneath are some of the most common Linux distributions such every bit:
- Debian
- Fedora
- Mandriva Linux
- openSUSE
- Arch Linux
- Gentoo
- Slackware
- Ubuntu
Its global use proves the fact that Linux is the virtually used operating organization. Over 80% of the cyberspace runs on Linux servers. More than then, about seventy-lxxx% of smartphones operate on the Linux operating system.
Content
- 1 Acme l Linux Commands With Examples
- ii 50 Linux Commands
- 1. cd Command
- 2. Alias Command
- 3. gyre Control
- 4. cat Control
- 5. df Control
- half dozen. chmod Control
- seven. diff Command
- 8. chown Control
- 9. echo Command
- 10. exit Command
- 11. find Command
- 12. uname Command
- thirteen. finger Command
- 14. gratuitous Command
- 15. grep Control
- 16. groups Command
- 17. gzip Control
- eighteen. whoami Control
- xix. top Command
- 20. tar Command
- 21. tail Command
- 22. sudo Command
- 23. SSH Control
- 24. head Control
- 25. history Control
- 26. kill Command
- 27. less Command
- 28. ls Command
- 29. human Control
- thirty. mkdir Command
- 31. shutdown Command
- 32. pwd Control
- 33. ps Command
- 34. mv Command
- 35. passwd Command
- 36. ping Command
- 37. Enable Control
- 38. Cp Control
- 39. Locate Command
- 40. Netstat Control
- 41. Cron Control
- 42. Traceroute Command
- 43. rsync Control
- 44. RPM Command
- 45. Ifup Command
- 46. Screen Command
- 47. Declare Command
- 48. Cpio Command
- 49. Exec Command
- l. Awk Control
According to the latest statistics, Android has a market share of 76% in the mobile OS. Android is developed from the Linux kernel, and the reason for its wide acceptance is that it is free and open-source. Apart from that, the Linux operating organization is prophylactic as Windows is more decumbent to viruses.
l Linux Commands
The Linux operating arrangement has countless commands but today we are only going to look at l commands that are frequently used by programmers. The best part of it is that it makes it easy to complete any chore.
i. cd Control
The 'cd' is one of the most common and basic commands used on Linux. The primary purpose of the command is to change the current directory. In simple words, its primary goal is to shift users to a new location in the file system. So, programmers can use 'cd' to change to a directory that is within the current directory. Users are required to blazon cd and the name of the other directory. For case, to go to the directory named 'office,' users tin type - cd part.
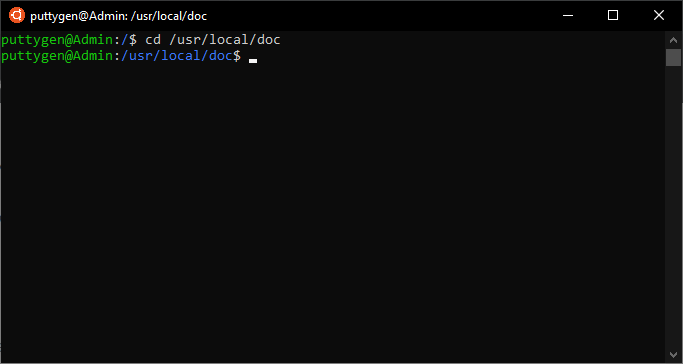
In instance, a user wants to move to a directory in the filesystem; then they need to enter the path of the directory. Users must remember to add a leading slash (/) when entering the path. Below is an example:
cd /usr/local/doctor
Now to get back to the home directory, a coder has to input the ~ (tilde) character. And so the control volition look like cd ~.
Permit'south view all commands in progressive order:
smith@puttygen: ~$ cd part smith@puttygen: ~/office$ cd /usr/local/medico smith@puttygen: /usr/local/doc$ cd ~ smith@puttygen: ~$
Users can also choose to use . . (double dots) to state the parent of the directory in utilise. Many use the double dot symbol to shorten the command. Below is an example of the same:
cd ../function
The cd command is very popular amidst Linux users. For example, users can type 'cd Downloads' to move from the home folder to the Downloads folder.
Note: Programmers exist cautious every bit the command is case sensitive and the user has to blazon exactly the same proper name as of the folder.
The cd command has a downside. Let's say the computer has a folder named 'Raspberry Pi.' In this case, the control cd considers lid second argument independently, hence resulting in an error. For such instance, coders can employ the astern slash equally a separator. Meet the example for the same:
cd Raspberry\ Pi
2. Alias Control
The command Alias is an astonishing way to personalize and organize all your commands. Information technology allows users to designate a name to a unmarried command or even a string of commands. And so programmers can give a curt name earlier executing information technology. Here is an example that uses an allonym:
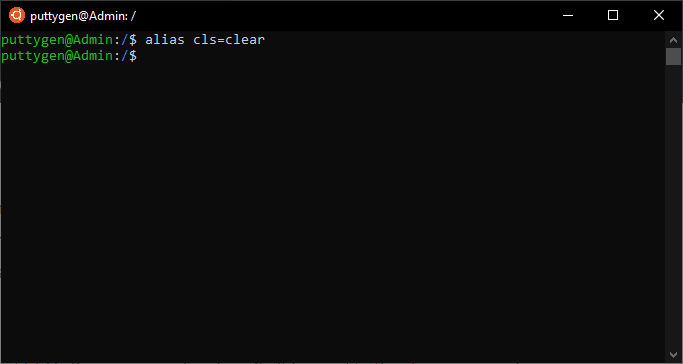
alias cls=articulate
The above control indicates that 'cls' is the new name for articulate. And then it is equal to the clear command, then whenever a user types cls, it will clear the screen. One of the master purposes of an alias is to save time, specially when some default control names are long. More so, personalizing commands helps when switching betwixt operating systems such as from Windows to Linux.
Also, programmers tin use an alias if they frequently misspell. For instance, if you type 'acb' while the actual command is 'abc.' Therefore programmers tin execute the post-obit control, which will make certain it takes both spellings as truthful:
alias acb="abc"
3. curl Command
The roll is a highly functional tool to recover data from URLs (Uniform Resource Locators) or internet repositories. The tool is not bachelor by default on many Linux distributions. For Ubuntu or Debian-based Linux variations, utilize apt-get to install the bundle. Other distributions have to use the package managers. Package managers terminate the need to install software and instead makes information technology automated manually. Beneath is the expression to install on Debian-based Linux variations:
sudo apt-get install curl
At present, let'due south await at the use of curl command. For instance, if a user wants to call up a particular file from the GitHub repository. While at that place is no official manner that GitHub provides simply instead users are forced to clone the unabridged database. Withal, using curl command, you tin quickly recover a single file.
To call up a file, users accept to state the exact file name to save it in. Programmers tin can leverage the -o (output) selection. Annotation: If a user does not use the -o choice in the control, then the files volition non exist saved on the calculator.
The post-obit single line of command volition retrieve the file a user wants:
curl https://raw.githubusercontent.com/smiths/linux/primary/kernel/events/cadre.c -o cadre.c
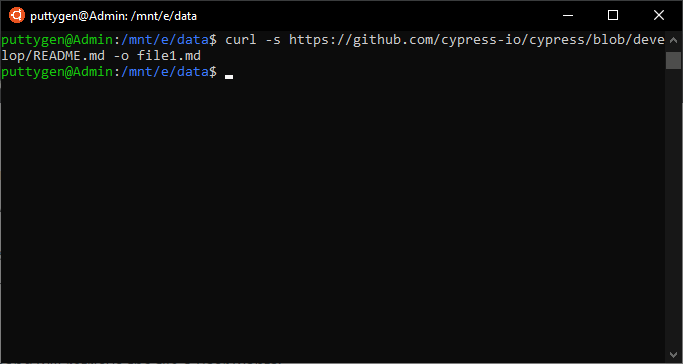
To avoid viewing the downloading progress or in other words hide it, users can utilise the -s (silent) pick. And then the new expression volition look as below:
gyre -s https://raw.githubusercontent.com/smiths/linux/master/kernel/events/core.c -o core.c
iv. cat Command
The true cat control is simple, and one of the most often used commands that are used in a variety of ways. It is short for 'concatenate' and permits users to create files, redirect output, listing the contents of a file, and even concatenate multiple files.
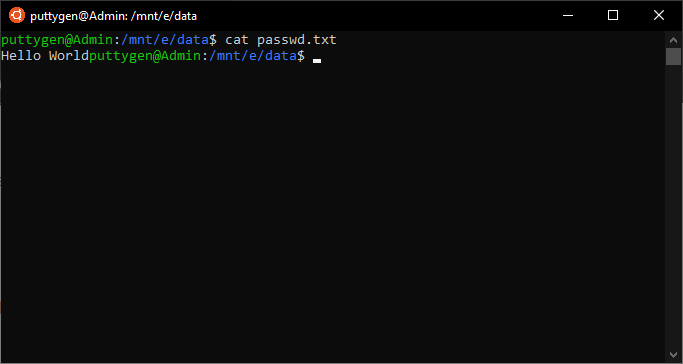
The command true cat is user-friendly and allows the user to accomplish many tasks with a single expression. For example, to view the content of the /abc/passwd file from the home directory, blazon the beneath command:
cat /etc/passwd
Next, type the post-obit to view the contents of multiple files, in this instance, test2 and test3:
cat test2 test 3
Now in case the content of a file is long and does non fit the terminal, then the user tin use the post-obit parameters:
cat test.txt | more
Now, if a user wants to see less, a user tin go back past typing the beneath parameter:
true cat tes.txt | less
Coders tin can likewise leverage the true cat control to view several lines in a file whose content is on the output terminal. To do then, a developer has to utilise -due north choice.
cat -n test.txt
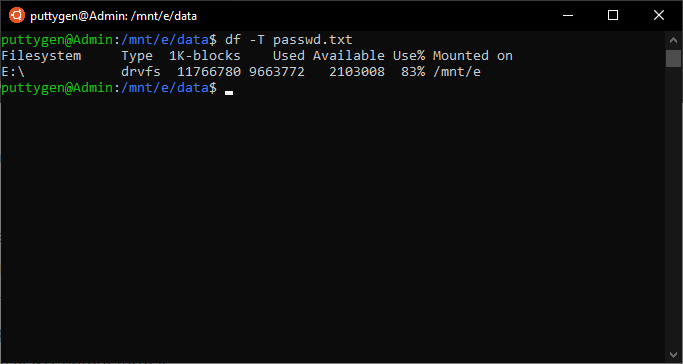
five. df Command
The df is a key command on Linux. Using df, coders can display the size, bachelor infinite, and used space on the filesystems of the device. It comes with multiple options, such as the following:
- -a, –all : it includes duplicate and files that are inaccessible
- -x: exclude specific filesystems
- -i, –inodes: it list inode information rather than that of cake usage
- -T, –print-type: prints the blazon of file system
- -P, –portability: information technology will apply the POSIX output format
- -B, –cake-size=SIZE: increase the size before printing the outcome
- -h, –human-readable: print sizes in power of 1024, which is Mb or Gb
- -H, –si: shows result in the power of 1000
- –total: omits all entries non relevant to available space, and presents the total
- -t, –blazon=Blazon: the issue is express to listing to file systems of a particular type
- –sync: invoke sync before the usage info
- -50, –local: limit listing to local file systems
The -h(human-readable) option displays size in Mb or Gb, rather than bytes. Meanwhile, the -x(exclude) choice allows uses to disbelieve specific filesystems.
vi. chmod Command
The chmod command allows users to alter or assign file permissions flags on a file or folder. The permission defines who tin read, write, or run the file. The code comes with references, which indicates to whom the permission volition be applicable.
Specific letters represent the references, and programmers tin use these letters to assign permission. Below is the list of letters:
- u - the possessor of the file
- g - this represents a grouping. So when assigned, it will apply to all members of the file'due south grouping.
- o - users who are not the possessor or a group member
- a - those who are all of the above
Then comes the 'modes' that represent each of the permission types. The post-obit are the permissions that a user can assign for a file:
- r - the letter means the user has the permission to the only read
- westward - the alphabetic character corresponds to write or delete the file
- x - the mode allows users to execute a file
Users tin can view permissions of all files using the -l command. It will listing file in the current directory. It will result in a cord of characters every bit follows:
-rwxrwxrwx
If its a file the output starts with '-' while for a directory it begins with.'
A series of iii messages represent each reference. Then the offset corresponds to the owner, followed by the 'grouping' and lastly for 'others.'
So, i can utilize chmod to give change or assign permission to either an possessor, group, or others. More so, the cord of characters is followed by digits which represent the specific type of file permission.
- 0: No permission is assigned
- 1: Execute permission
- 2: it has to write permission
- three: the user has write and execute permissions
- iv: users can only read with this permission
- 5: users take read and permission to execute
- half-dozen: it indicates that yous have both read and write permissions
- 7: information technology offers you to exercise anything with the file such as read, write and execute
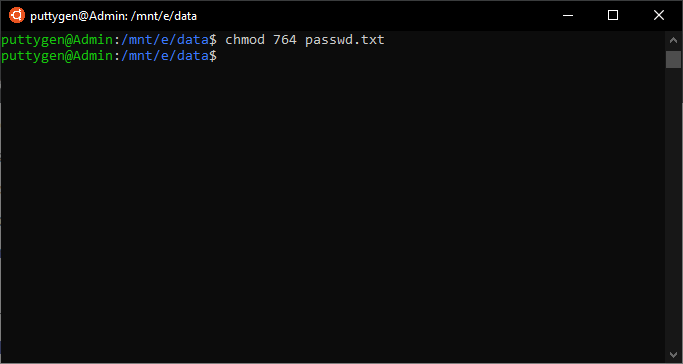
Looking at our case.txt file, we can see that all 3 sets of characters are rwx. That ways everyone has read, write, and execute rights with the file. Programmers can use the digits with the chmod control to assign permission. For instance, to give the possessor complete permission - read, write and execute, to provide a group read and write permits and read-only permission to others, enter the following command:
chmod 764 exam.txt
7. diff Control
The diff command comes in very handy for those that deal with organizing a lot of data. The command will compare data between 2 text files and display the deviation. Coders can piece of work in many ways to customize how the data is displayed.
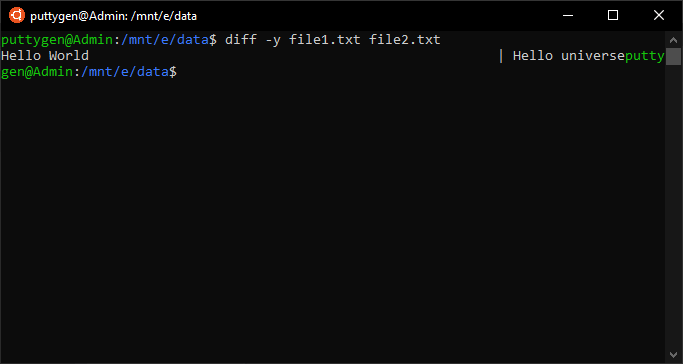
The control comes with two options, which are -y and -w. The -y is a fashion to display the difference between two files side by side. Meanwhile, the -w is the option to decide the maximum line width to ensure the lines don't need wraparound.
Programmers can utilize --suppress-common-line to prevent the unequal from listing the same lines. Therefore, you tin put their attending to just view the lines that are different.
For example, nosotros have to compare ii files named - smith1.txt and smith2.txt.
The command volition look like equally follows:
diff -y -West seventy smith2.txt smith2.txt --suppress-common-lines
8. chown Command
The chown command is frequently used and is very uncomplicated to execute. Information technology allows users to change the owner and the grouping possessor of a particular file. Let's showtime list the file using the ls -50 that will describe the owner and group possessor of the file.
~work$ ls -l
The code will list files with owners and group owners.
-rwxrw-due west-1 smith smith 7655 April 25 17:26 trial.txt
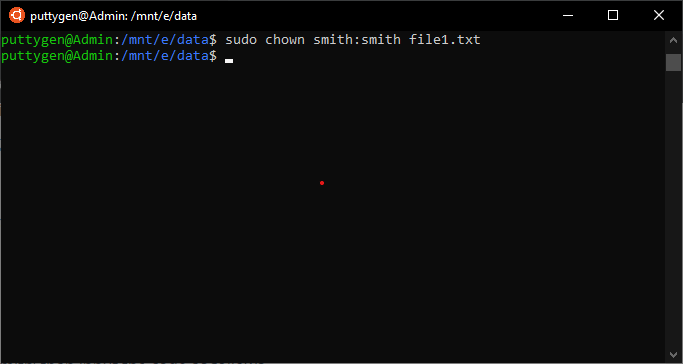
In this example, 'smith smith' is the owner and grouping owner, respectively. All users have a default grouping, and it also indicates that the file is not shared with whatever other grouping. Using chown i can change the file owner and even the possessor of a group. Coders have to use sudo to change or retain it dorsum to the previous owner.
sudo chown smith:max trial.txt
Now to change even the possessor and the grouping, input the post-obit
sudo chown max:max trial.txt
In case, user wants to revert to 'smith' than input the code as follows
sudo chown smith:smith trial.txt
ix. echo Control
The echo command is leveraged to print a string of text passed as an argument to the terminal window. It comes every bit the built-in command and is oftentimes used get output condition text in shell scripts. For example, a user wants to impress 'play with a string of text' in the concluding, then it volition wait something like this:
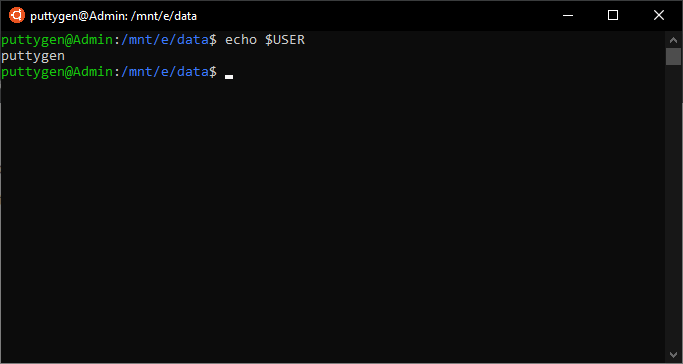
echo play with a string of text
More and then, one tin can even use echo to print the value of environment variables such as user and path of a file. For instance, if you desire to know the user, home directory, or path, and so enter the following command:
~$ echo $USER ~$ echo $Domicile ~$ echo $PATH
The echo is also one of the nearly essential and crucial commands when it comes to shell scripts. Programmers can utilize the command with a script to print or display the progress or status of a script while it is running.
ten. exit Control
The exit is the near basic command of all. All it does is go out the shell in which it is active, close the terminal and even logs out of an SSH remote session. Coders tin utilize the exit control with or without parameters. So to close the terminal users has to enter the following command:
~$ exit
Now, let's look at an instance with a parameter. For instance, users have to enter the post-obit command to use exit with the assist parameter:
~$ get out --assist
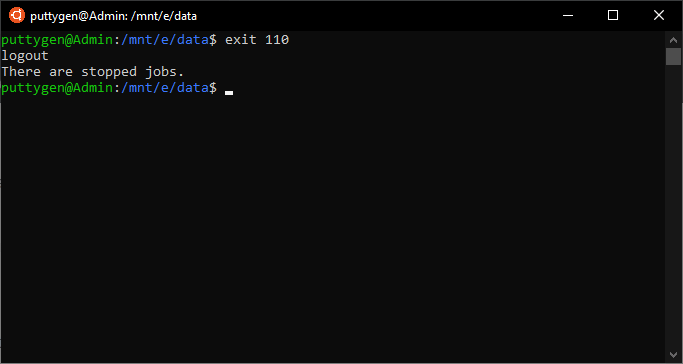
Coders should besides use information technology with render status to ensure there are no errors at the time of closing the file. So the user tin type the post-obit command:
~$ exit 110
If the return value is '0', then the script or programme is executed without errors. Meanwhile, if the render value is '1' then it the program consists of some mistakes.
11. find Control
The find control is one of the most useful commands on Linux. Information technology is common not to know the location of files, and therefore, coders can run the find command to look for it. The merely prerequisite from the user is to type in what to look for and where. More so, yous can also utilize parameters to make the search more than specific. Enter the following command to find a file:
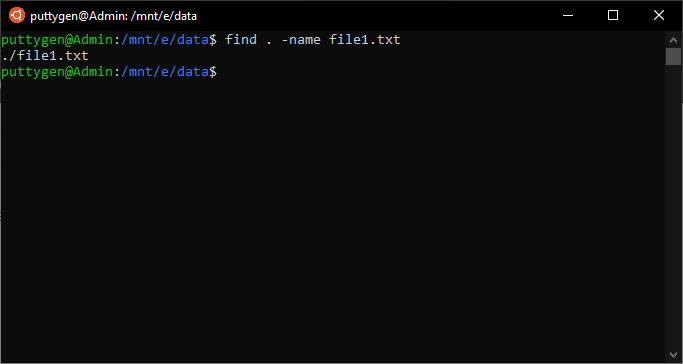
~/Documents$ find . -name *smith*
The higher up command tells the terminal to notice files that match the blueprint. The * looks correspond to the sequence of messages or characters. Even so, if a user wants to represent a unmarried alphabetic character than they tin use ? (question marker character) instead of *.
The above command will as well include directories. In case you just desire to look for only files, then programmers take to use the -blazon option. Let's look at the command:
~/Documents$ find . -type f -name *smith*
The 'f' represents the files.
Users likewise have the selection not to brand the search case sensitive. Users have to enter the command as follows:
~/Documents$ find . -type f -iname *smith*
12. uname Command
The uname command provides users with the system information of the Linux system or computer they are using. It comes with several options that enable users to view all or specific data they desire. Below is the option programmers tin can use with the uname command:
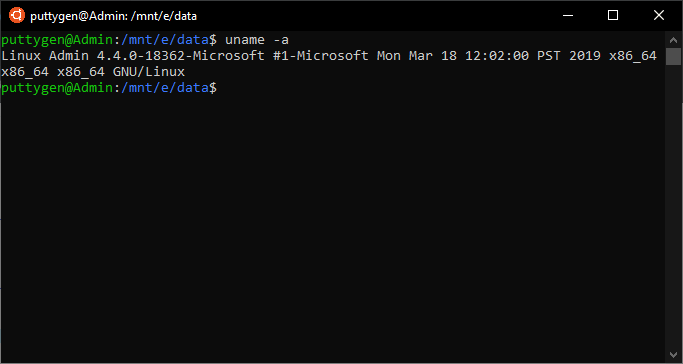
- -a = you can utilize this option to encounter everything
- -s = with this option users can view the kernel information
- -v = the option allows 1 to run into the kernel version of the arrangement
- -r = the parameter lets one view the kernel release
Therefore the control looks something every bit follows:
uname -a uname -southward uname -five
thirteen. finger Command
The finger command is leveraged past programmers to wait upwards and obtain cursory information on users. It presents various data such as total proper noun of the user business relationship, real name, latest login information, idle fourth dimension, write condition, office location, and user's domicile directory.
It also concatenates with multiple options such every bit -due south, -l, -p, and -m. With the -s option, one tin can view all the data about a user mentioned above. Yet, using the -l, presents information about login shell, contents of file and mail status, in addition to all data provided with -s option.
The -p option is used to obtain information nearly the contents of the ".plan," ".project," and ".pgpkey" files.
Meanwhile, the -m option stops from matching usernames. Users must recall that the matching by finger command is case sensitive.
Beneath are basic examples using finger command:
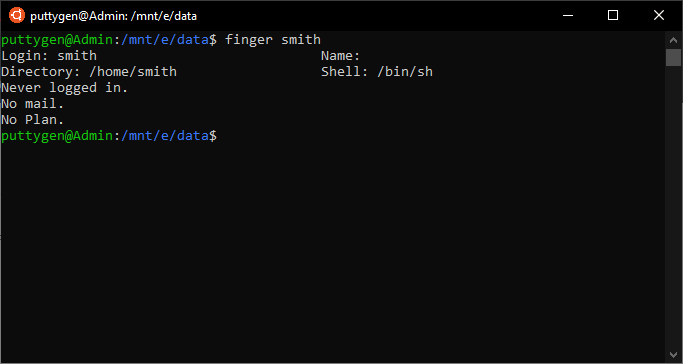
~$ finger smith
The command displays information about the user 'smith.'
Now to view the contents of a file of the user, programmers tin use the following control:
~$ finger -p smith
14. gratuitous Command
The costless command-line utility provides users with a summary of the total available gratis infinite on the computer. More so, it also displays the total amount of used memory of the Random Admission Memory (RAM) and the swap memory on the computer. Using the free command will besides present the buffers leveraged past the kernel.
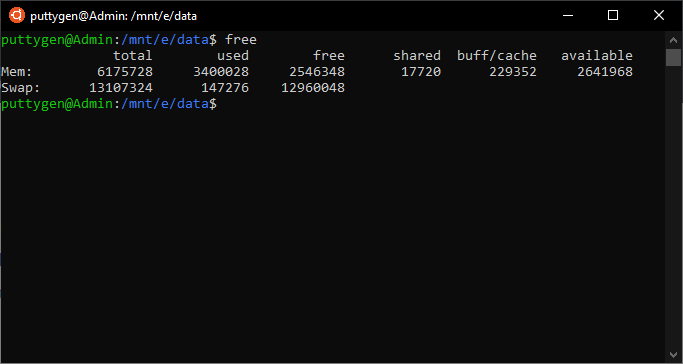
The output of the command displays information in bytes. However, coders can use the -h option to ensure the data is provided in human-friendly numbers. Values. Here is the example of the costless control:
~/Documents$ complimentary -h
15. grep Command
The grep command is 1 of the most useful commands on Linux. It is an acronym, and its full class is; global regular expression print.' The sheer capability makes it a frequently used command on Linux. The grep command looks for lines and prints the ones that match a predefined search pattern.
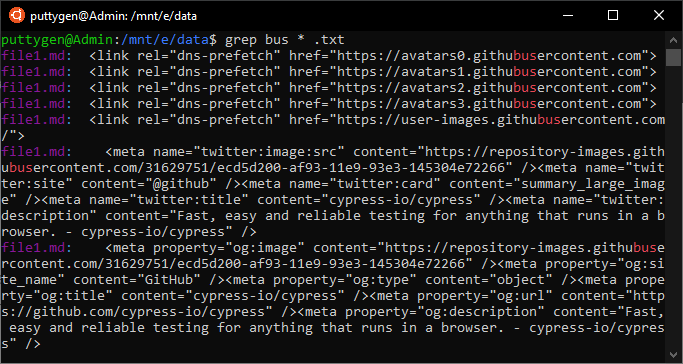
Normally, most programmers apply grep control to search for a detail string of words in a given file. More so, y'all tin use the programme to search for contents of the files. So for example, you have to enter the post-obit command to wait for the word 'coach' in all text files in the active directory:
~/Documents$ grep omnibus *.txt
The result will show list non only the name of the file merely also display the line it matches. The matching text is highlighted, making it easy for the user to await for the file on the calculator.
16. groups Control
Linux has to mechanism two manage users - users and groups. In simple words, the groups are a collection of users. A group makes information technology easier to manage user with aforementioned permission privileges.
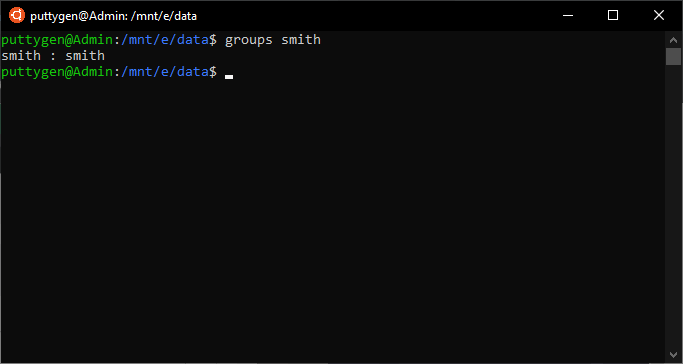
The groups' command is every bit uncomplicated equally it sounds. It provides information about groups that a user is a member of. In simple words, when the control is executed, information technology will brandish the name of primary and supplementary groups for a username. The simple command looks like this:
~/Documents$ groups smith
In instance, the user does non specify a username; then it will print group membership for the active or electric current user. More than so, for better agreement, you tin also use the --help control with groups. And so it will look something like this:
groups --help
17. gzip Command
The gzip is a useful command when information technology comes to file management. It is a file compressing tool with its primary goal is to reduce file size. The gzip command past default deletes the original file and saves but the new compressed file which is resulted from the control.
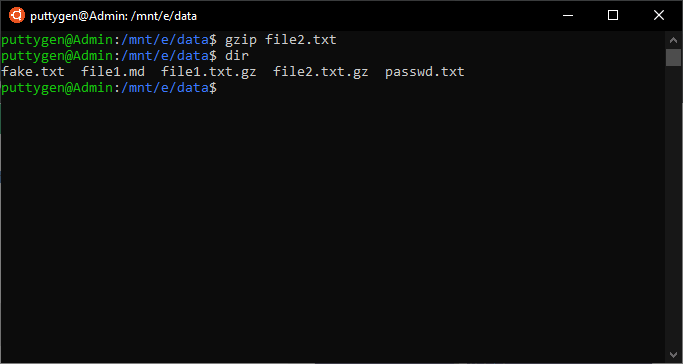
Still, you can use the -k (keep) option to ensure that the original file is not deleted. The gzip command will look equally follows:
~/Documents$ gzip -k instance.c
Users tin can fifty-fifty revert the file to decompress format. To do so, you have to apply the gunzip command and the original file will available at the location.
18. whoami Control
The whoami control is simple and mostly comes handy for amateur Linux users. It tells the user with a username they are logged in as. More and then, coders tin use the control to know if anyone has logged into an unnamed Linux terminal. It is straightforward to execute and is one of the few commands in Linux that perform a unmarried task.
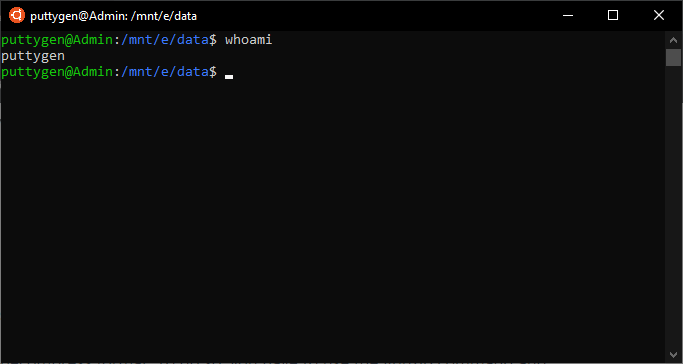
~/Documents$ whoami
The output will show the username of the one that is logged in as. Autonomously from Linux and other Unix-based operating systems, the command is also standard for the Windows operating system. Coders can use the control with two options help (--assist) and version (--version). Similar commands include the 'westward' and 'who.'
~$ w
Users can combine it with multiple options to filter users on the Linux system. For example, if you want data on a specified user, then programmers accept to enter the following command
~$ w user
19. meridian Control
The height command is a job management program that presents a existent-time display of CPU and memory usage of the Linux computer. It is a simple status summary. The control is suitable for those who like to monitor the CPU functioning of the Linux machine. The user but has to blazon 'tiptop' in the final to run it.
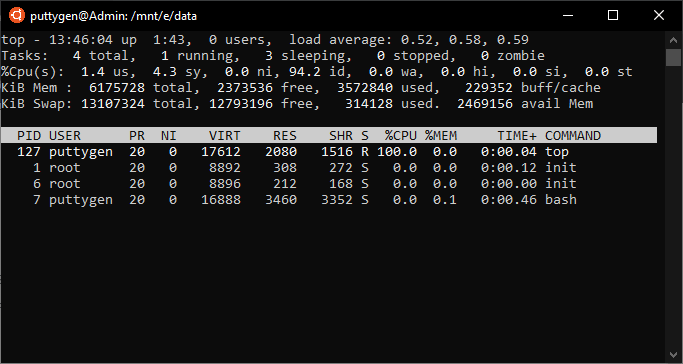
It displays the number of users that are logged in, the runtime of the computer and the load average for diverse time intervals such equally five and fifteen minutes. It as well provides a summary of the job. The overview consists of the current condition of the chore, such every bit if they are running or sleeping or stopped. Below are letters that ascertain the statuses of the process:
- R: Running
- D: Uninterruptible slumber
- S: Sleeping
- T: stopped (often known every bit Traced)
- Z: Zombie
The command volition present other data in a column format. Here is what each column stands for:
- PID: process ID
- USER: the Username of the owner of the process
- PR: priority of the procedure
- NI: the nice value of the procedure
- VIRT: this defines the amount of Virtual memory consumed by the procedure
- RES: resident retentivity ingested past that process procedure
- SHR: shared retention used
- S: it provides the condition of the process
- %CPU: the amount of CPU time consumed by the process
- %MEM: the share of concrete memory leveraged
- Fourth dimension+: composite CPU time used by the task
Past default, the digits do not come in a human-readable format, just users tin can press 'E' to convert information technology to man-friendly values.
Press 'Q' to go out from the tool after reviewing all data.
20. tar Command
The tar command is one of the nigh useful accounts when it comes to file management. Using tar, you lot tin can create archive files that tin perform as storage for multiple files. The archive file is often known as the tarball.
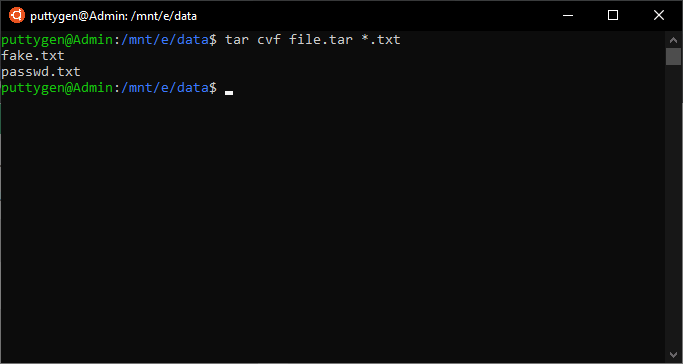
Using tar makes file management convenience every bit one tin can share a collection of files chop-chop. You can even use the command to excerpt files from archives and likewise compress the annal. User must demand compress files otherwise the command will archive file in an uncompressed version.
Users have to define what files will the archive file have and the proper name that a user wants to requite. For case, let'due south say we desire to create an annal for the Football directory, then enter the following command:
tar -cvf videos.tar Football/
In the case, the -c is the choice to create, the -five is the verbose option that provides feedback while they are added to the annal.
Meanwhile, the -f is the filename that coders want to give to the annal. In this example, information technology is videos.tar.
21. tail Control
The tail command is a command-line utility that lists the last lines of a file that are given via standard input. The number of output lines is fix to 10 past default. However, users tin can modify it by combining the tail control with the -n (number) option. Programmers can use tail even to track files in real-time. Information technology means that a user can view new lines as they are being written. Allow's wait at the tail command as information technology is in default:
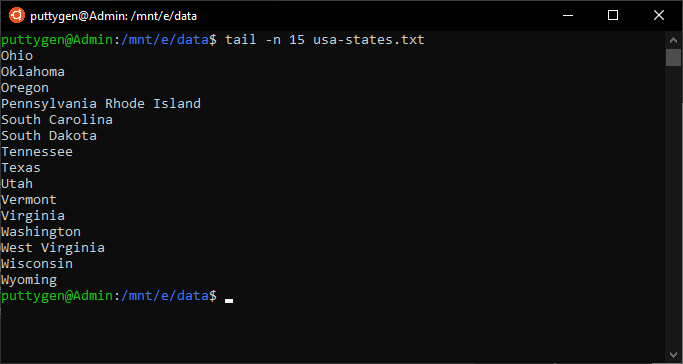
~/Documents$ tail example.txt
At present in case a programmer only wants to view the latest five lines, so one has to enter the following command:
~/Documents$ tail -due north five example.txt
22. sudo Control
The Sudo command is one of the most avant-garde Linux commands. While the syntax is basic, but dealing with it is critical as information technology requires root access. The most common use of the sudo command is to change the password for other users. For instance, if Smith wants to change the password for Max, so the command will exist as follows
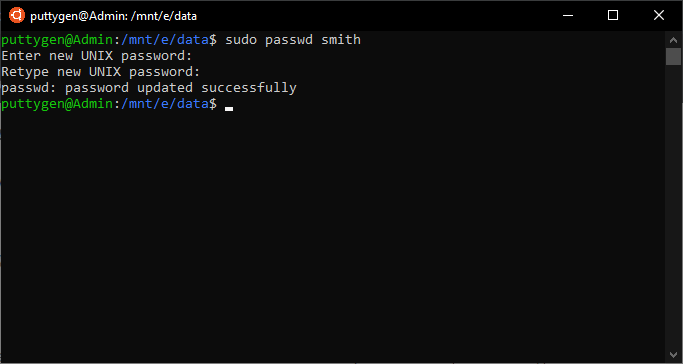
~/Documents$ sudo passwd max
The terminal will prompt Smith to input his countersign and so allow the alter. The reason i must be cautious is that it will enable yous to operate programs using the security privileges of some other user. Coders can use the -l (list) option to know which commands is permitted and not permitted on the current host.
~$ sudo -l
23. SSH Command
The SSH command allows users to connect to remote Linux machines. You tin can fifty-fifty log into your account on the remote computer using the command. User has to provide a username, domain name, IP accost of the remote machine to make the connectedness. Let's look at the example below:
~$ ssh Max@192.168.3.82
Using the command, Max is connecting to a remote auto whose IP is 19.168.three.82. It will demand to enter the password, and once verified and logged in; then the prompt will modify to a system that the developer is using. If Max writes the 'w' command, then it will list all the users of the arrangement. As Max is continued via a remote motorcar, the connectedness type will land as 'pts/1'. The pts/1 is a pseudo-terminal slave that displays that it is non directly continued to the bodily computer.
To logout from the remote system, y'all have to blazon the exit command.
~$ leave
24. head Command
The head command provides users with the first lines of the file. By default, the output is ready to the kickoff x lines. However, users can alter it past using the -north (number) option. The head is the contrary of the command, which provides the final 10 lines of a file. In the first instance, we will blazon the default command.
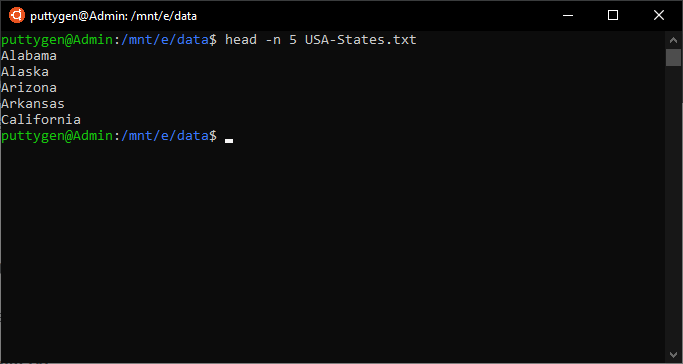
~/Documents$ head -instance.txt
Now, let's see the command if we want to limit the output to simply the offset 4 lines.
~/Documents$ head -n 4 example.txt
The command is standard amongst many of the Unix-line operating systems. The command also displays piped data. You lot can likewise use the head control to impress the offset 10 lines of multiple files.
caput -due north 5 example.txt example2.txt
25. history Control
The history command is a way to view the commands that a user has inputted previously on the command line. The default limit is set to display only the latest five hundred commands. It is an piece of cake style to echo the commands merely by inputting ! (exclamation) the point with the number of the command that the user wants to repeat from the listing.
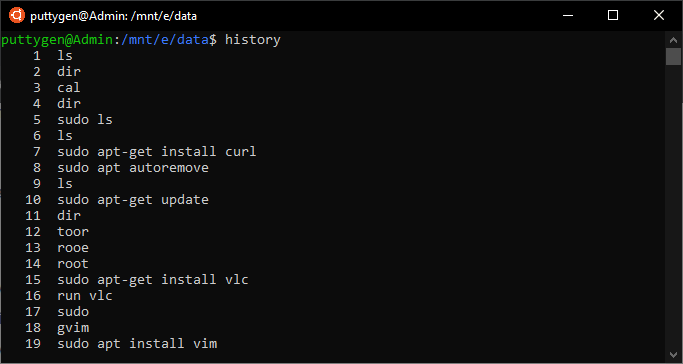
~/Documents$ !180
The above will repeat the 180th command from the list. It is very useful because a user tin avoid typing the command again. In instance you desire to repeat the concluding inputted command than ane has to only input '!!' points. Coders can also look at the command history from the .bash_history in your folder.
26. impale Control
The kill command offers the liberty to end the process from the command line. It is useful for those monitoring CPU processes as information technology makes it easy to terminate processes without working on it manually.
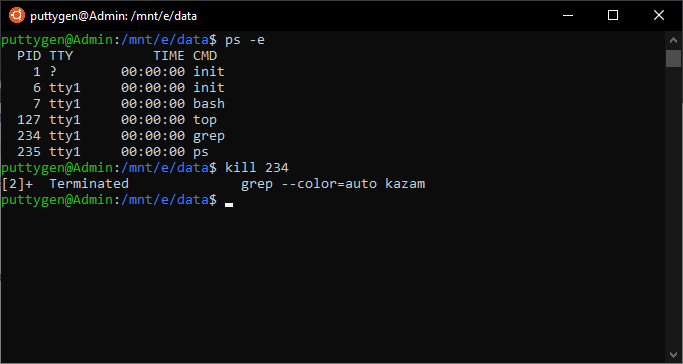
The user is only required to enter the Process ID(PID). Users must be cautious non to kill process randomly or haphazardly. But utilize the kill control if the process or task must terminate or has locked upwards. To obtain the process ID, users have to apply the ps and grep command.
ps -e | grep Kazam
The command will display the Process ID; in this case, it is 1702. Now that we take the Process ID, allow's impale the Kazam screenshot program.
~$ impale 1702
27. less Command
With the less command, ane does not have to use an editor to view files. It allows users to view files without fearing it being modified. The procedure is faster and best for those who believe their files might mistakenly be edited.
Output of above command
Once the file opens, users can view the entire document using the Up and Downward central on the keyboard. Programmers can as well make employ of the PgUp and PgDn keys. Once viewed, users tin quit less past pressing the 'Q.' Below is an instance of the less command:
less case.txt
Coders tin can likewise use the less command from a list of files on the entire hard drive.
ls -R / | less
To navigate forward press '/' key and to move astern press '?'.
28. ls Command
The 'ls' is the most bones and probably i of the beginning commands anyone learns. It is a unproblematic command to list the directory of files and directories. The ls command will list files in the agile directory if the user does non specify other. Information technology is one of the most frequently used commands as users tin concatenate its various options.
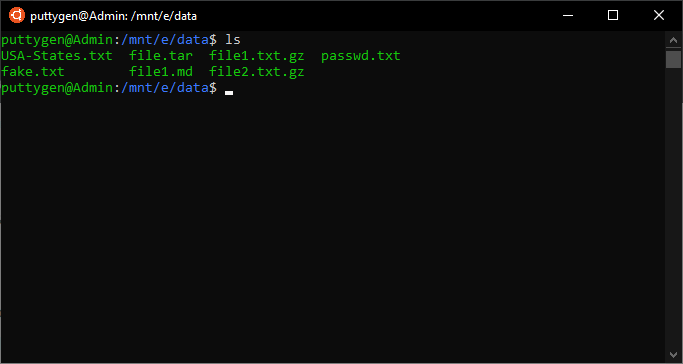
~/Documents$ ls
The above control volition list all files in the current directory. For a comprehensive list, coders accept to use the -l(long) choice and use the -h(human being) option to ensure the file sizes are mentioned in a human-readable format.
~/Documents$ ls -lh
In case, a user also wants to view subconscious files, and then enter -a (all files) parameter:
~/Documents$ ls -lha
To modify the list in club of latest updates, enter the post-obit control:
~/Documents$ ls -lt
29. man Control
The man control displays the 'human pages' or user transmission a command. It is advantageous as the programmer who is new to commands volition accept a better understanding before executing any Linux commands.
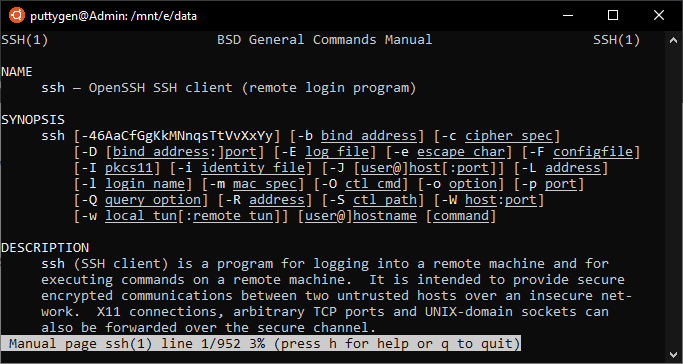
The man command provides a complete detail such every bit Name, return values files, examples, authors, and more. Users can leverage the capabilities of the less command equally the 'human' control uses it to nowadays the transmission. For instance, to view the manual of SSH control type the following:
homo SSH
Navigate the manual using the PgUp and PgDn keys. In instance a programmer can't understand the document than they have to press 'h' for assist. Printing 'q' to quit from the manuals.
thirty. mkdir Command
Using the mkdir command, coders are able to create new directories. Many operating systems refer to directories as folders. A coder only has to provide the name of the directory, and mkdir will create it. It can besides create multiple directories simultaneously and even set up permissions for the same.
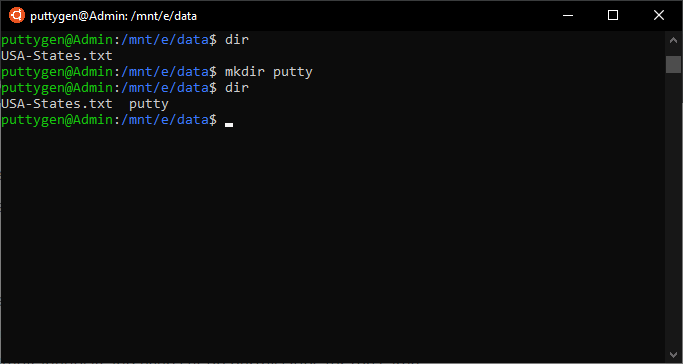
Programmers must also know that they take to provide a path for the new directory in case it is going to be placed in some other directory than the electric current one. Let's create a new file named 'examples.'
~/Documents$ mkdir examples
Now if the user wants to create a new directory dubbed '2020' inside the 'examples,' then enter the following command:
~/Documents$ mkdir examples/2020
With mkdir, users can create a directory without the existence of its parent directory. To do then, you take to use -p(parents) option. For example, you want football game as the parent directory of '2020,' but information technology does non exist, then 1 can execute the command as follows:
~/Documents$ mkdir -p examples/football game/2020
Even though 'football game' does not be, the mkdir control will create all of information technology.
31. shutdown Command
The shutdown command is simple equally it sounds and near users volition come beyond as soon equally they larn most Linux commands. As the proper noun sounds, the shutdown command will switch off or close downward your Linux system.
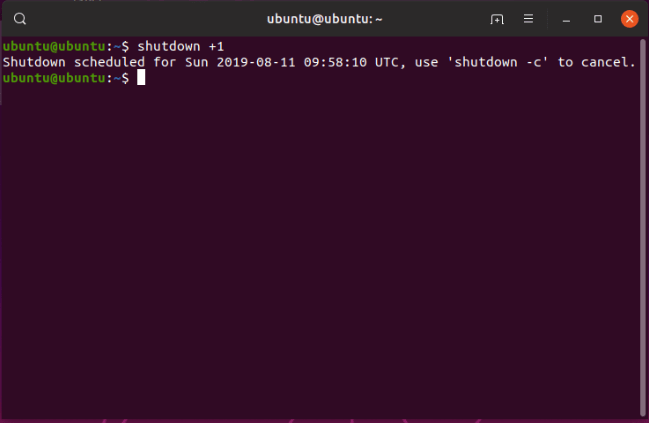
There are various parameters you tin can use with the shutdown command, but if no parameter is specified, and so the computer will close down in i minute.
~/Documents$ shutdown
In case you lot are in a rush and wants to close down the computer immediately, then employ the 'now parameter.'
~/Documents$ shutdown at present
Users tin fifty-fifty schedule shutdown and also notify all users for the same with a single command. The but matter users are to provide is the time and the pc will shutdown equally per scheduled. You can also schedule in minutes, such as 10 minutes from now. Below are both examples:
~/Documents$ shutdown tonight at 22:00, don't forget to salve your work and savour the weekend! ~/Documents$ shutdown +x
Employ the -c(cancel) option to cancel the scheduled shutdown.
~/Documents$ shutdown -c
32. pwd Command
The pwd command is uncomplicated every bit it can get. Its master output is to print the active (in-use) directory commencing from the root/directory. It is an acronym and stands for Print Working Directory. The pwd command will print the full arrangement path of the current directory. More than so, $pwd is an environment variable, which means it will store the path of the active directory. It comes with two options, which are -L and -P.
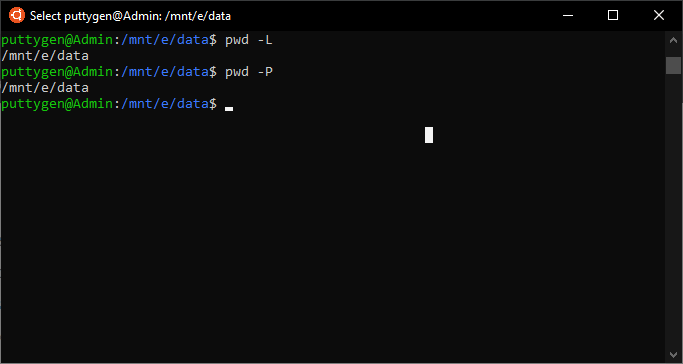
- -Fifty = it will print a symbolic path
- -P = information technology will impress the bodily full path
~/Documents$ pwd
To view the bodily path, input the following command
~/Documents$ pwd -P
33. ps Command
The ps command displays a procedure that is currently running on the Linux car. It provides a existent-time display of all active processes. The ps command provides a basic summary of the procedure that includes its Process ID. In many operating systems, the procedure is referred to as tasks. By default, the ps control will list agile operations in the current shell. Even so, you tin can utilize options to change to different shells.
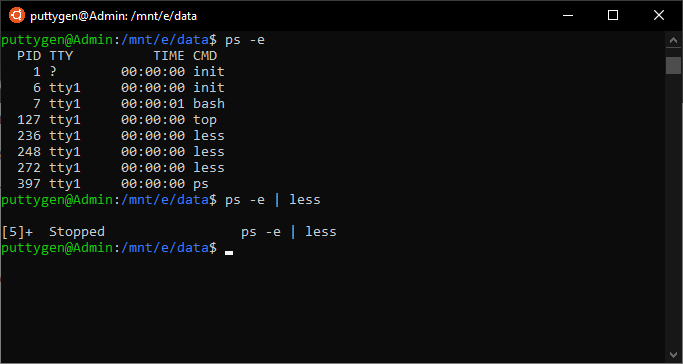
~/Documents$ ps
In case, a user wants to view the process of a specific user so they can add -u(user) option to the ps control.
~/Documents$ ps -u smith
The listing would exist very long, and hence you tin cut it brusk past adding the less command.
~/Documents$ ps -u smith | less
Use the -e(every process) to view every running process.
~/Documents$ ps -e | less
34. mv Command
The mv command enables programmers to shift files and directories betwixt other directories. It is notwithstanding another file management command that makes organizing data easy and straightforward. Users can also utilise the control to rename files.
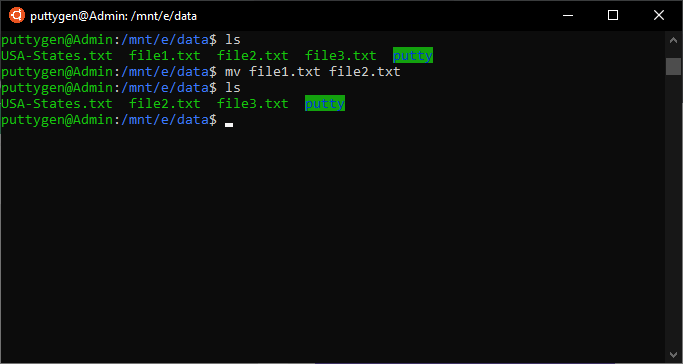
The only affair that the user has to define is the name of the file and where information technology needs to be moved. For instance, let's move a file dubbed 'examples.pdf' from '~/Document/Football game' directory to the current directory. The current directory is delineated using . Graphic symbol.
~/work$ mv ~/Documents/Football/examples.pdf .
You can fifty-fifty rename file using the mv command.
~/work$ mv examples.pdf test.pdf
Users can even achieve both tasks, i.e. moving the file and renaming it in a single command.
~/work$ mv ~/Documents/Football/examples.pdf ./examination.pdf
35. passwd Control
With the passwd command, users can modify the password for a user. It not just lets you change your password but also of other users. The passwd command is besides one of the most frequently used Linux commands. The command comes in very handy as it makes it very easy to change the password for anyone in the team. To change others password, users have to apply sudo command as it requires permission privileges. Blazon paaswd to change your ain password
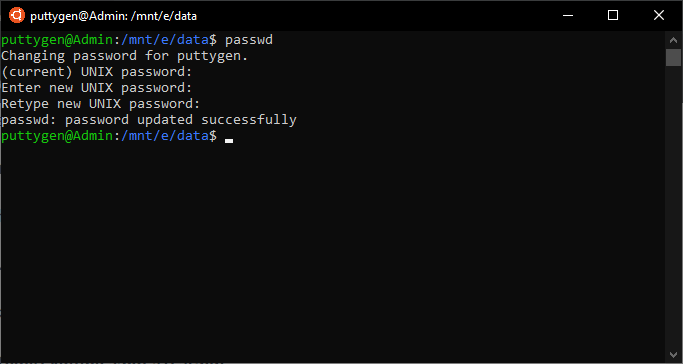
~/work$ passwd
To alter others password, type the following:
~/piece of work$ sudo passwd max
It will demand the user to enter their ain password. In one case verified, the new passwords for other users.
36. ping Control
With ping control, users tin can verify if the network connectivity status between computer and source over an IP network. More than so, you can view the response fourth dimension from a network.
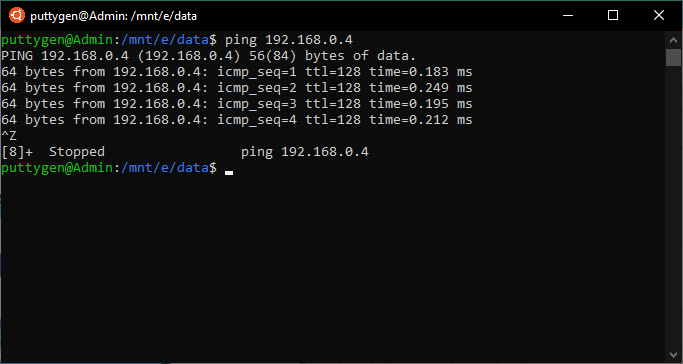
The response fourth dimension is the fourth dimension it takes to send and receive a response from the network. One of the near mutual uses of the ping control is to troubleshoot networking issues.
Coders have to provide an IP address to run the command. Below is how you tin can execute the ping command:
~/work$ ping 192.168.3.18
The ping runs unceasingly, and hence a user has to press Ctrl+C to cease it. Withal, you can use the -c(count) option to ping information technology for a specific number of attempts.
~/piece of work$ ping -c 5 192.168.3.eighteen
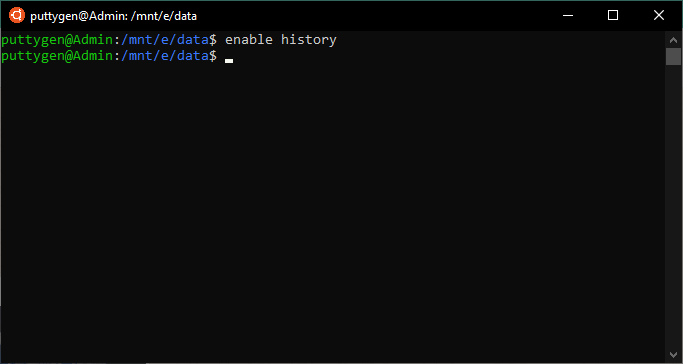
37. Enable Control
The enable control is a built-in crush command akin to the disable command. Coders use the enable to initiate the printers or classes, and similarly utilizes the disable selection to cease the printers. Programmers tin can utilize the control with various options as listed below:
- printer: information technology refers to the printer that has to be enabled
- -a: it will list and display if built-ins are enabled or disabled.
- -c: the option terminates whatsoever active impress requests
- -d: it will delete a builtin that has been loaded with
- -W: it will not disable printer and await till the request is not printed. Programmers must note that they tin can't utilise this and -c selection together. The -Due west option will not work for remote printers.
- -r reason: the options will classify a specific purpose to disable the printer.
- -n: by default names are enabled so that this choice will disable it.
An example of the enable command will look as follows:
~$ Enable printit
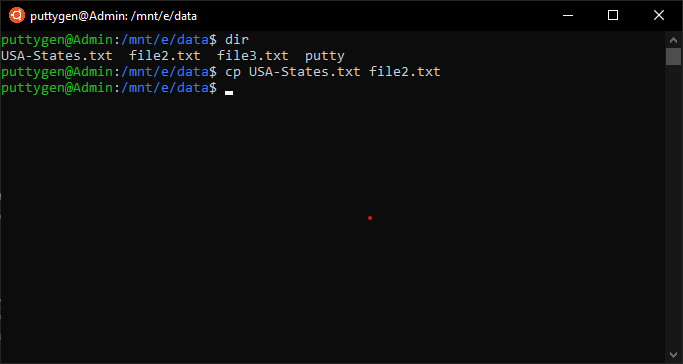
38. Cp Command
The cp command is standard beyond many of the Unix-similar operating systems. Information technology stands for re-create, and its primary part is to copy files and directories. Coders can even re-create multiple files or directories using cp.
Each cp statement must have two filenames as information technology creates a mirror image of the file on a deejay with a different name. The control-line utility tin can fifty-fifty motility files or folders. Programmers can likewise choose to backups of files.
Wait at the below code to re-create a file using cp command:
~$ cp me.txt you.txt
In the higher up example, the file me.txt volition is copied to some other file named you.txt. As mentioned above, the cp file will create a mirror file of the original file as part of the process.
Programmers tin can't copy directories directly every bit it will end upward in error. Therefore, they are required to pass the -R flag. The -R flag will, therefore, re-create a folder and then create a re-create. Let's have every bit an instance that football is the directory and i has to copy it. Input the following argument to do then:
~$ cp -R directory/ football
39. Locate Command
In Linux, the ii almost stiff and widely used commands to search for files are 'discover and locate.' While detect is good without a uncertainty, the locate command is more powerful and presents results faster than the find command. Therefore, for instantaneous results, there is no better command-line utility than 'locate.'
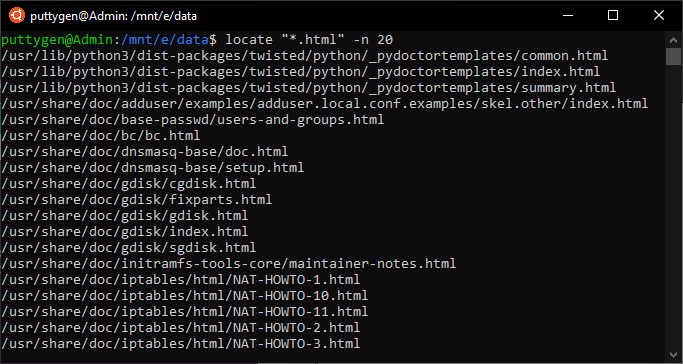
The reason locate command is faster is because information technology searches file through the database opposing to file command which initiates a search through the file system. The database has $.25 of files that issue in an almost instantaneous issue.
Executing the locate command is straightforward to use and one has to do is pass the name of the file. Allow's see information technology in action in the below case.
~$ locate me.txt
There are various options inside the control, such as searching for matching entries.
40. Netstat Command
The netstat is a command-line tool that presents an overview of the network connections. Across that, the command besides provides several network interface statistics, multicast memberships, routing tables, and masquerade connections.
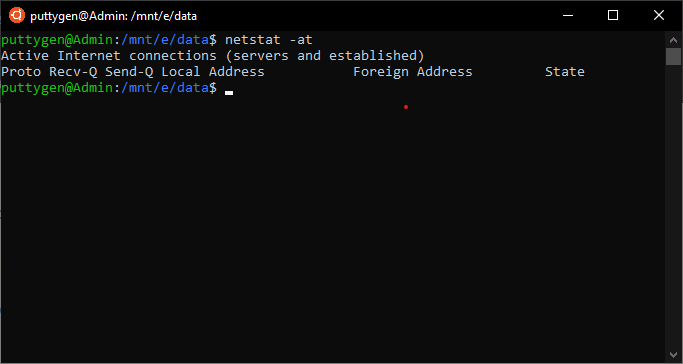
Although it is standard on UNIX-like systems, many other operating systems also have netstat command.
Below are a few examples using the netstat command:
~$ netstat -a | more
The command will display listening and not-listening sockets. Users can always utilize the -interface option to view only the interface that is down.
Programmers tin can use netstat to list specific ports such as simply list tcp or UDP ports.
Enter the following to view TCP ports:
~$ netstat -at
To just view UDP ports, use the below argument
~$ netstat -au
You tin even choose to view the statics of all ports. Input the following command display overview of all ports:
~$ netstat -due south
41. Cron Command
The cron command is a software utility that is provided by Unix-like operating systems. The master chore of the utility is to schedule the job at a predefined time. Cron is a compelling and popular command that many uses to schedule task periodically at predetermined time or dates.
The time-based job scheduler automates scheduling making information technology very convenient. The cron runs in the background and is often referred to as a daemon process. Daemon process is a background process that runs for a long fourth dimension and answers requests for services. The all-time feature of cron is that it performs its task without the intervention of a user.
Commonly almost programmers use cron to accomplish repetitive tasks automatically. To complete this repetitive job is daunting, and hence, coders tin schedule processes to run automatically. Users can even schedule processes such equally organizing folders at given time intervals, taking backups at regular intervals, and likewise checking for updates.
Beneath are few basic cron commands:
crontab -e = the command runs crontab
crontab -50 =you tin can edit crontab with this argument
crontab -r = it displays contents of the crontab
sudo crontab -u -eastward = using this control it will un-schedule all crontab tasks
Allow'due south view an instance whereby crontab takes a backup at a given fourth dimension interval.
00 02 * March Tuesday/habitation/max/backup.sh
The above command takes a fill-in of the folder every Tuesday in March at 2 AM.
42. Traceroute Command
The traceroute command tracks the route that a item bundle of information takes to reach to the host. In elementary words, the command prints the journey that a parcel takes from the source to destination.
One of the nearly mutual purposes to use traceroute is to track where data is lost in the network. As such, that coders can identify the detail node that is down.
To better understand, let'southward track the route that a packet takes to reach Google from your estimator. More so, the traceroute command will also display all jumps it makes during the journey.
Coders also accept various options that they can use with the traceroute command.
~$ traceroute -4 10 google.com
The higher up command uses the IPv4. Meanwhile, the below command uses IPv6.
~$ traceroute -half dozen x google.com
Users can also utilize the -g(gate) option to route the packet through the gateway.
~$ traceroute -g 192.168.43.45 google.com
43. rsync Command
Rsync stands for Remote Sync is a very standard command leveraged to synchronize files and directories. The software utility is usual among many Unix-like operating systems. The primary purpose of the utility is to sync files between hosts or machines, both locally and remotely. Beyond that, Rsync is also used to copy files.
The rsync utility can piece of work in 2 ways sync information, which are as follows:
- Sync to/from another hose using remote shells such as SSH.
- Sync via Rsync daemon leveraging TCP.
Programmers tin can even employ various options with the Rsync command
- five: verbose
- -z: it compresses file data
- -r: the option allows users to copy information recursively, just information technology does non save permissions.
- -a: with this option, users can copy files in the archive style and even save permissions and timestamps.
- -h: the pick offer data in a homo-readable format
Below is a basic example of transferring files between 2 local machines. In the case, we copy a file dubbed examples.tar to /tmp/football/ folder.
~$ rsync -zvh examples.tar /tmp/football game/
Below is the statement to re-create/sync a folder - test, to or from a server:
~$ rsync -avz test/ root@192.168.1.105:/home/
44. RPM Control
RPM stands for Red Lid Package Manager, which is a tool that permits users to install, verify, manage, and uninstall software packages in Linux and Unix-like operating systems. However, programmers must call up that the utility only works if the software is developed using the .rpm format.
The tool has five basic modes, which are every bit follows:
- Install: information technology install RPM packages
- Remove: coders can use this mode to uninstall or remove RPM packages
- Upgrade: with this way, ane can update RPM packages available on the system
- Verify: coders tin use to verify whatever RPM bundle
- Query: it is usually used to query any RPM package
The control below volition list all RPM packages on your Linux car:
~$ rpm -qa
Users can enter the following argument to see if RPM is installed or non on a package. Coders have to apply the -q pick.
~$ rpm -q BitTorrent
45. Ifup Command
The ifup control is an essential and straightforward way to bring the network interface up and enable it to transfer and receive data. In other words, coders use the ifup command to configure network interfaces. Programmers must take note that the command is used with Sudo as it deals with permission privileges.
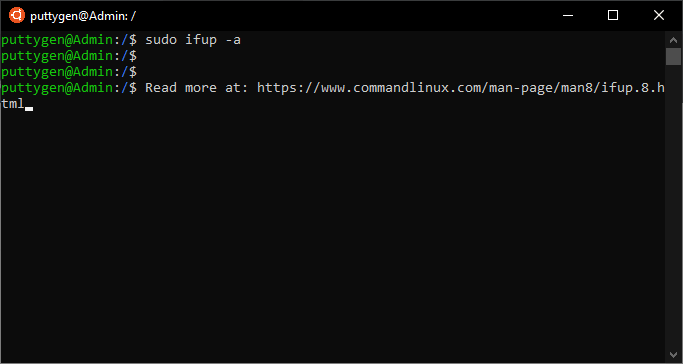
For instance, to get the network interface up to use this control.
~$ sudo ifup -av
Users can employ the beneath options with the control:
- -a(–all): if coders use this option so they must note that it will apply to all interfaces labeled as automobile.
- –forcefulness: the option permits users to force configuration of the interface.
- -V: the pick prints the data of the version in use
- -v: verbose the result every bit they are performed
46. Screen Command
The screen control permits users to initiate multiple beat sessions via a single ssh session. The best feature of the screen command is that the process can exist detached from a session and then join the session again at a later period. It is possible every bit the procedure because the screen runs the process that was started even afterward beingness discrete.
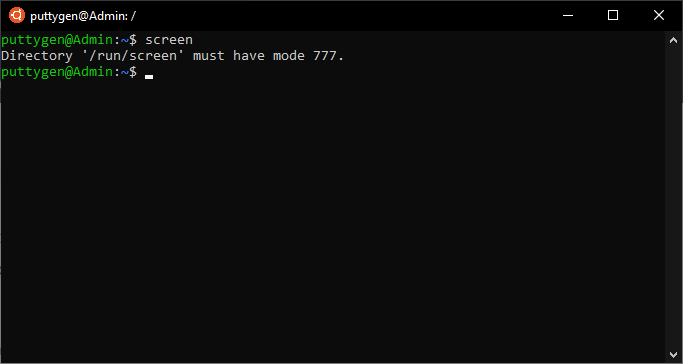
Therefore, making information technology possible to reattach the session at a after time. And so one can begin the same identify where they left off in the terminal.
The below command will install 'screen':
~$ sudo apt install screen
Typing 'screen' will launch a window inside the screen.
~$ screen
The command volition initiate a new window within the screen and also give the windows it a proper name.
~$ screen -s examination
47. Declare Command
The declare is a fustigate beat builtin command which means that it is a part of the shell. It has multiple purposes, such as declare shell functions, display variables, and more.
Coders can use the control with various options listed below:
- -p: the selection shoes options and attributes of every variable name that used name arguments.
- -f: it is considered as the name of the function and not every bit a variable.
- -F: using this choice, coders tin choose not to view the contents of the function but rather simply the attributes and role's name.
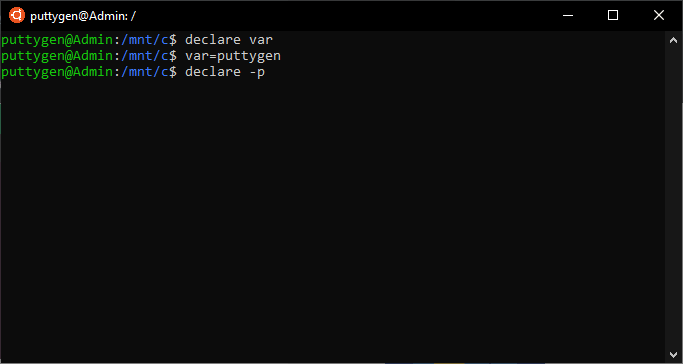
The beneath case shows how to declare a variable:
~$ declare var
Coders can apply the command to view the variable name of each attribute:
~$ declare -p
48. Cpio Command
The cpio command is a standard amidst many Unix-like operating systems with the primary purpose being processing annal files. In simple words, programmers can use the cpio command to re-create files from archives such as .cpio or .tar.
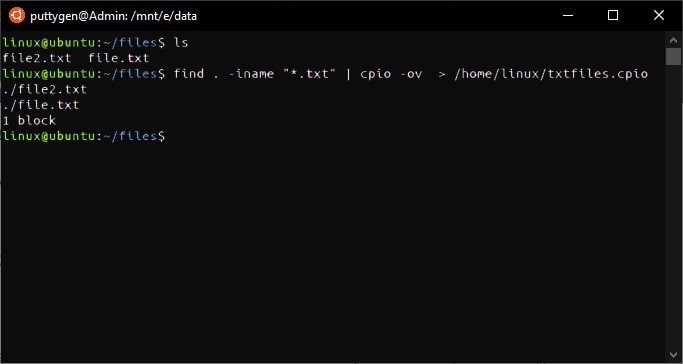
Let'due south view an case to extract a .cpio file. The command volition extract files and directory with a single argument.
~$ cpio -four < /document/linux/example.cpio
Programmers can even create .tar files using the cpio command as below:
~$ cpio -ov -H tar > /certificate/linux/examplefile.rar
Similarly, coders can even employ cpio to excerpt .tar files. Beneath is an instance of how to excerpt the 'examplefile.rar.'
~$ cpio -iv -F /certificate/linux/examplefile.rar
49. Exec Command
The exec command is leveraged to run a command directly from the fustigate. Therefore it does create a new process but instead substitutes it with the command that has to be executed. Then, if the argument is successful, so information technology won't come up back to the calling process.
Programmers can use the exec with various options listed below:
- c: users can execute a command with an empty surround
- a name: programmers can use the option to pass a name
- 50: it passes dash as the zeroth argument of the command
The exec can be used every bit an argument or without a control. Below is an example of the exec:
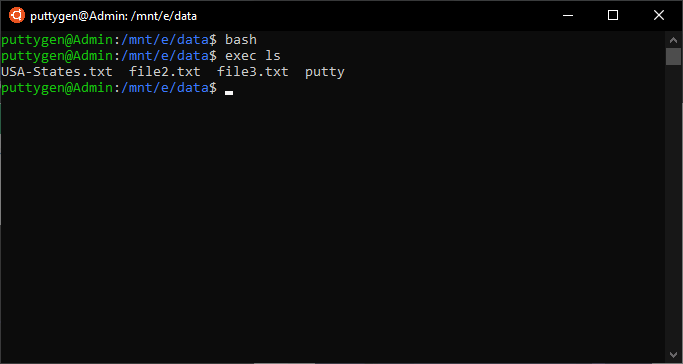
~$ bash ~$ exec ls
50. Awk Control
Awk is a software utility that one can leverage to write pocket-sized programs in the way of statements. Users can employ these statements to define text patterns which can be searched in a certificate. One of the principal purposes of Awk is to scan patterns and processes.
Awk is actually a scripting language that is mostly leveraged by programmers to dispense data. With Awk, coders do non have to use compiles but tin can run scripts with logical operators, variables, and cord functions.
Below is an example of using awk. First, nosotros utilize it to impress all lines in a file.
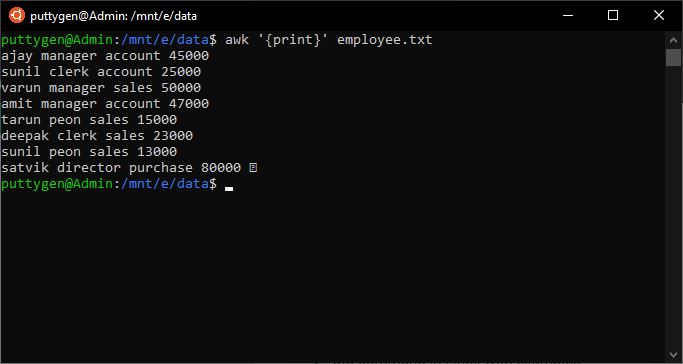
~$ awk '{print}' team.txt
Now let's try to requite the expression pattern.
~$ awk '/strikers/ {impress}' squad.txt
Download Linux Commands PDF
We will shorty upload a linux commands pdf file to download for free. Meantime, you lot tin can bookmark this folio for all linux commands.
The commodity covers most of the basic Linux commands that one will come across. There are diverse other commands, just commonly the above listed l Linux commands volition do the chore. More so, running commands on Linux is all about combining it with the correct option. There are multiple ways to get the job done, and one must use logic to choose the all-time possible option.
etheridgeapprokill.blogspot.com
Source: https://www.puttygen.com/linux-commands
0 Response to "Which Command Can Be Used to Determine a User's Most Recent Log in?"
Post a Comment